Categories
Tags
8ksec 8ksec.io aidl android anti-debug anti-frida anti-hook APK broadcast-receiver bypass CC certification config content-provider CTF ctf cybersecurity cybertalents deep-links deeplink dex dexclassloader dylib dynamic-analysis dynamic-loading emulator exam exploitation file-encryption flutter frida ghidra hextree.io hook hooking http-security ios ipc ISC2 jailbreak-detection Kali kiosk-mode logic-bug mobile mobile-exploitation native network-interception pentest plugin privacy proxy-detection rce reverse-engineering runtime script security smali sql-injection static-analysis swift tls-pinning token-extraction url-parsing url-scheme vulnerability web webview writeup WSL2
61 words
1 minutes
8kSec.io iOS Challenges Writeups
My n00b Journey Through iOS Security Challenges
Welcome to my writeup series for the 8kSec iOS Application Exploitation Challenges. As a n00bie in iOS Security, I’m documenting my journey through 11 vulnerable iOS applications that cover everything from password managers to privacy tools. Each challenge teaches different exploitation techniques including reverse engineering, dynamic analysis, and vulnerability discovery. Will it be easy? :“D
8kSec iOS Challenges
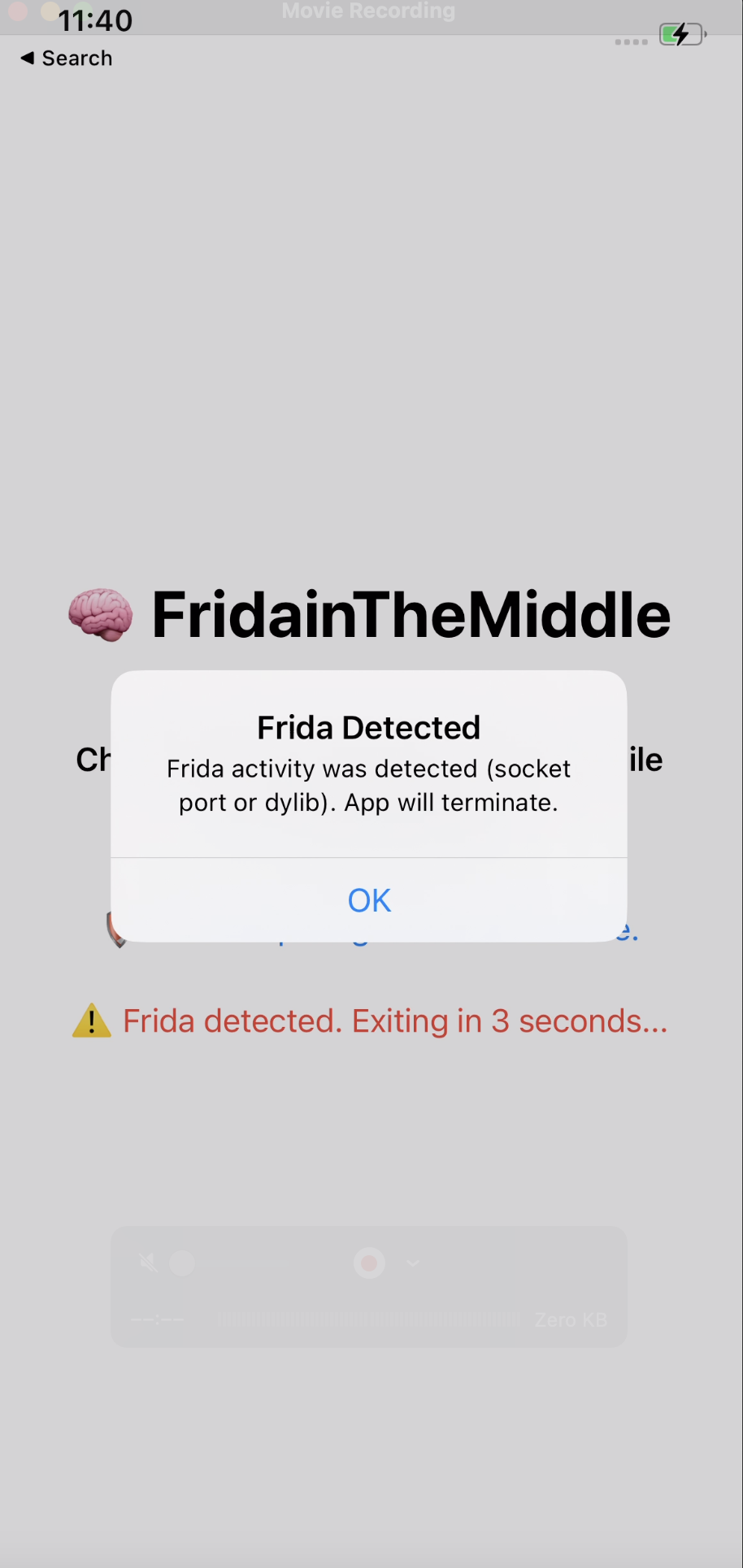
Challenge 01: FridaInTheMiddle
Bypassing iOS anti-frida/anti-hooking using only dynamic analysis
864 words
|
4 minutes
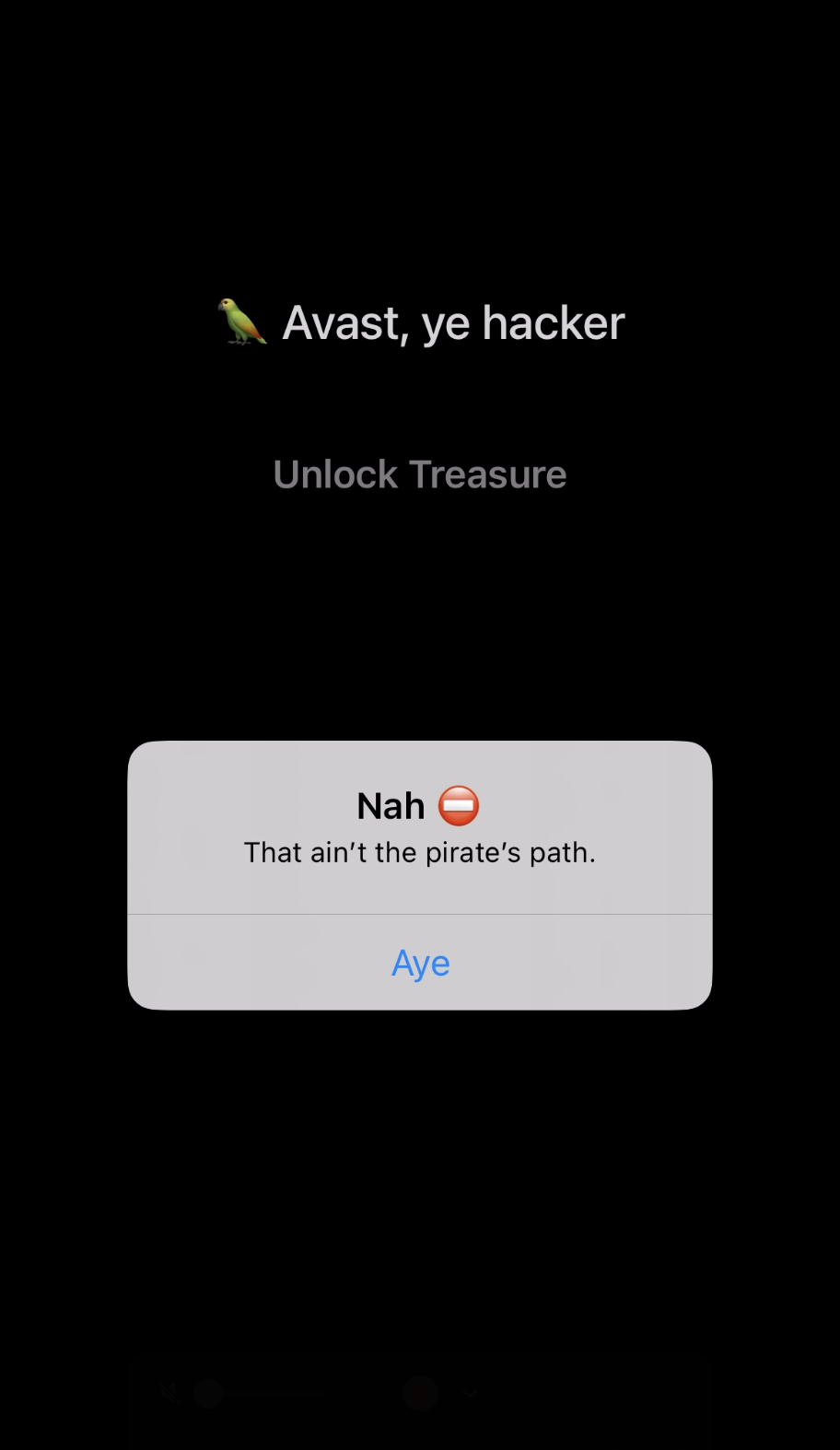
Challenge 02: SwizzleMeTimbers
A pirate-themed iOS app with a secret buried deep inside its view controller. A simple button reads “Unlock Treasure”, but it’s protected by a method that always returns false
1059 words
|
5 minutes
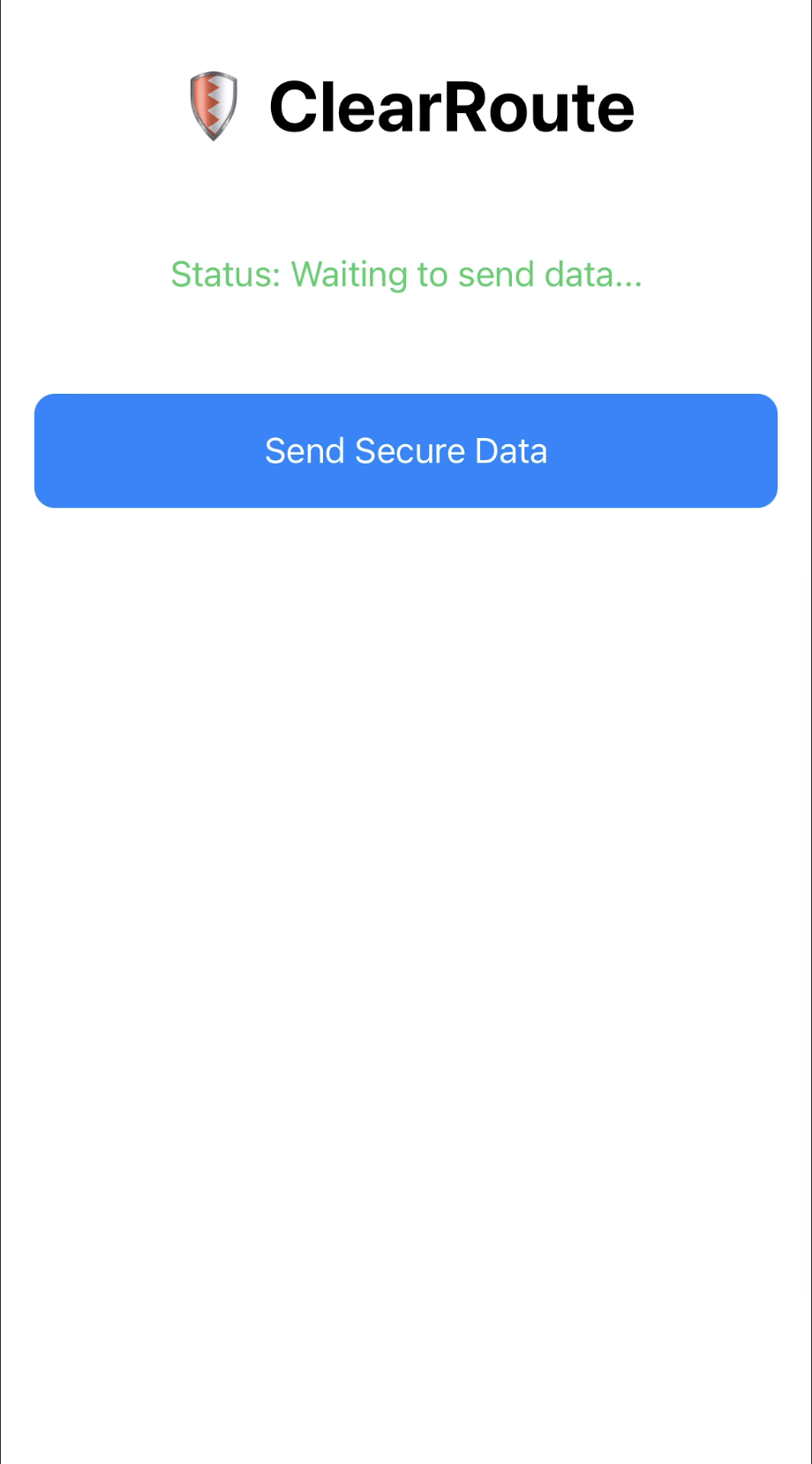
Challenge 04: ClearRoute
2025-11-17
A walkthrough on bypassing client-side anti-analysis checks in a Swift iOS app. This writeup covers how to defeat a common proxy-detection mechanism using Frida to hook and manipulate the runtime, allowing for successful network interception.
918 words
|
5 minutes
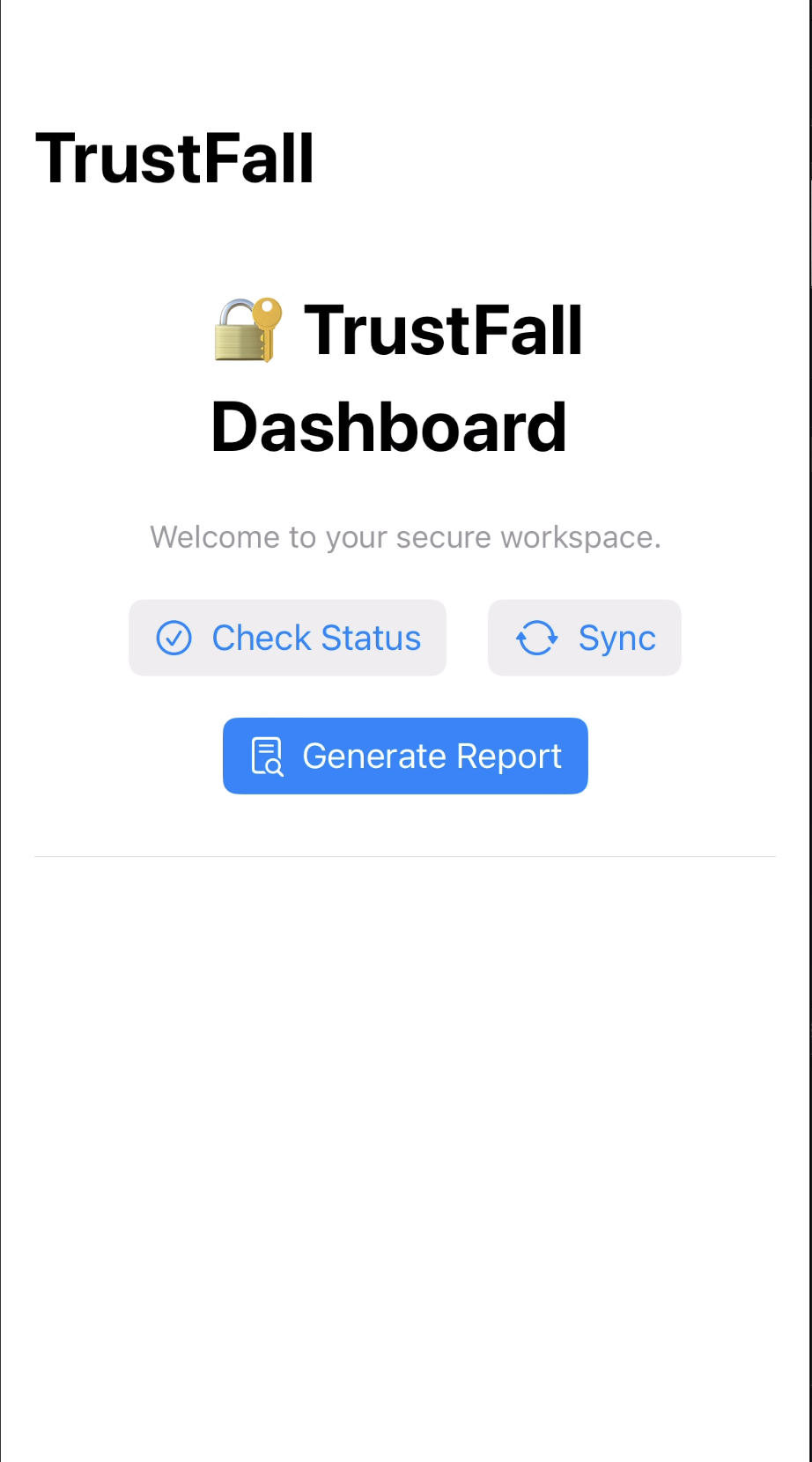
Challenge 05: TrustFall
2025-11-18
A walkthrough on reverse engineering an iOS app to bypass deep link sanitization checks. It demonstrates using static analysis to identify logic flaws and exploiting URL parsing inconsistencies to defeat domain restrictions.
862 words
|
4 minutes